Research Vision
Towards Reliable Society 5.0: People-centric Super-smart Society Towards Society 5.0 proposed by The Cabinet Office (CAO), designing systems for humans by incorporating the cyber space and the physical space, namely, designing sophisticated cyber-physical-human systems (CPHS), is presently one of the most important issues. Meanwhile, threats to our society by cyber attacks have been getting more severe monotonically. A report has shown that the monetary loss from cybercrime in 2020 is estimated to be about 945 billion USD (cf. McAfee). Furthermore, with the advance of their incorporation, in addition to traditional information systems, physical systems including critical infrastructures have been becoming attractive to criminal organizations as a target of cyber attacks. In fact, manufacturing was the second-most attacked industry in 2020, and second only to financial services (cf. IBM). Several incidents that had seriously damaged actual systems have been reported, such as Uranium enrichment plants in Iran, Ukrainian power grids, and a US fuel pipeline system. Those attacks led to shutdown of the systems, and as a result, even safety of our life was threatened. My ultimate goal is to develop reliable Society 5.0 through research on secure CPHS design.

State-of-the-Art Security of Cyber-Physical System (CPS) Security of cyber-physical systems (CPS), or control systems, has been intensively studied in this decade motivated by incorporation of information and physics. For example, in 2015, a security guideline for industrial control systems has been published by the National Institute of Standards and Technology (NIST) in the US. In addition, especially in Japan, Control System Security Center (CSSC) was established in 2012. Thanks to their efforts, main issues on CPS security have been summarized, and it has been recognized that novel defense technology is needed to be developed in addition to traditional IT security methods. In academia, many researchers in the control field have devoted themselves to research on CPS security using the tools developed in the community so far (cf: survey paper from MIT).
Emerging Issue: Interaction among Information, Physics, and Humans However, a statistic has reported that 90 percent of actual cyber attacks are based on phishing, password leakage caused by reuse, and re-exploitation of known vulnerabilities (cf: IBM). Those entry points, which cannot be captured only by observing the system behavior, are rooted on humans who are responsible for management and operation. This fact suggests that we need to explicitly take human factors, emphasized in the concept of Society 5.0, into account in addition to connection between information and physics. CPS behaviors have been investigated in control engineering and relevant areas, while human behaviors have been investigated in social science, such as behavioral economics and cognitive psychology. I aim at resolving the issue on CPHS by combining knowledge accumulated in the fields.

Approach: Mathematical Formal Method For the issue above, I adopt mathematical formal method, namely, describing the subject in a quantitative manner and analyzing consequences deductively. In particular, the strengths of mathematical approach for CPHS security are as follows: 1. Common Language in Physics, System Engineering, and Economics CPHS is an interdisciplinary field composed of Physics, System Engineering, and Economics. Although those interests are not necessarily overlapped, it is common that the fundamental laws are written mathematically. Consequently, mathematical representation can a natural language in CPHS to seamlessly bridge the knowledge discovered in each field. 2. Formal Verifiability Risk assessment is a fundamental step towards secure system design. Since security halls can be supposed for any system indefinitely, risk cannot be evaluated uniquely, and the premises that made in each scenario are needed to be clarified for security verification. In this regard, mathematical approach explicitly states the premises as mathematical assumptions in the discussion. 3. Synergy with AI AI (artificial intelligence) plays a central role in security of the next generation society. Since its behavior is described mathematically, the knowledge obtained through researches on CPHS security is expected to be expanded to defense using AI, such as ML (machine learning), by describing the results mathematically.

Application Example: Smart Grid Towards carbon neutrality committed at Paris agreement, smart grids, where renewable energy resources are used as baseload power, have rapidly been developed. A challenging problem to develop smart grids arises from huge uncertainty of the power generated by nature. To enhance power supply stability, novel measuring and actuating devices are required, such as AMI (advanced metering infrastructures), WAMS (wide area measurement system), PMU (phasor measurement unit), and SI (smart inverter). Those devices are connected over an information network, and as a result, the entire system composed of the electrical grid with the physical and the information networks becomes a large-scale CPS. In case of any contingency, although local response such as switching of transmission lines is carried out automatically, global response such as restoration of the entire grid is carried out manually by operators inside the control center. Hence, humans' decision making crucially affects the system's behavior in smart grids. Moreover, as the liberalization of electricity retail sales becomes common, the electricity market becomes active, whose effects to the grid cannot be ignored. The main entity in a market is humans, and its design, namely, mechanism design is a traditional field in economics. As observed above, smart grids, where its components interact each other in a complex manner, are a typical example of CPHS. Moreover, since smart grids are fundamental infrastructure supporting our life, its security is an extremely important issue. From those perspectives, I particularly pay attention to smart grids as a specific application example in my studies.
Specific Research Topics
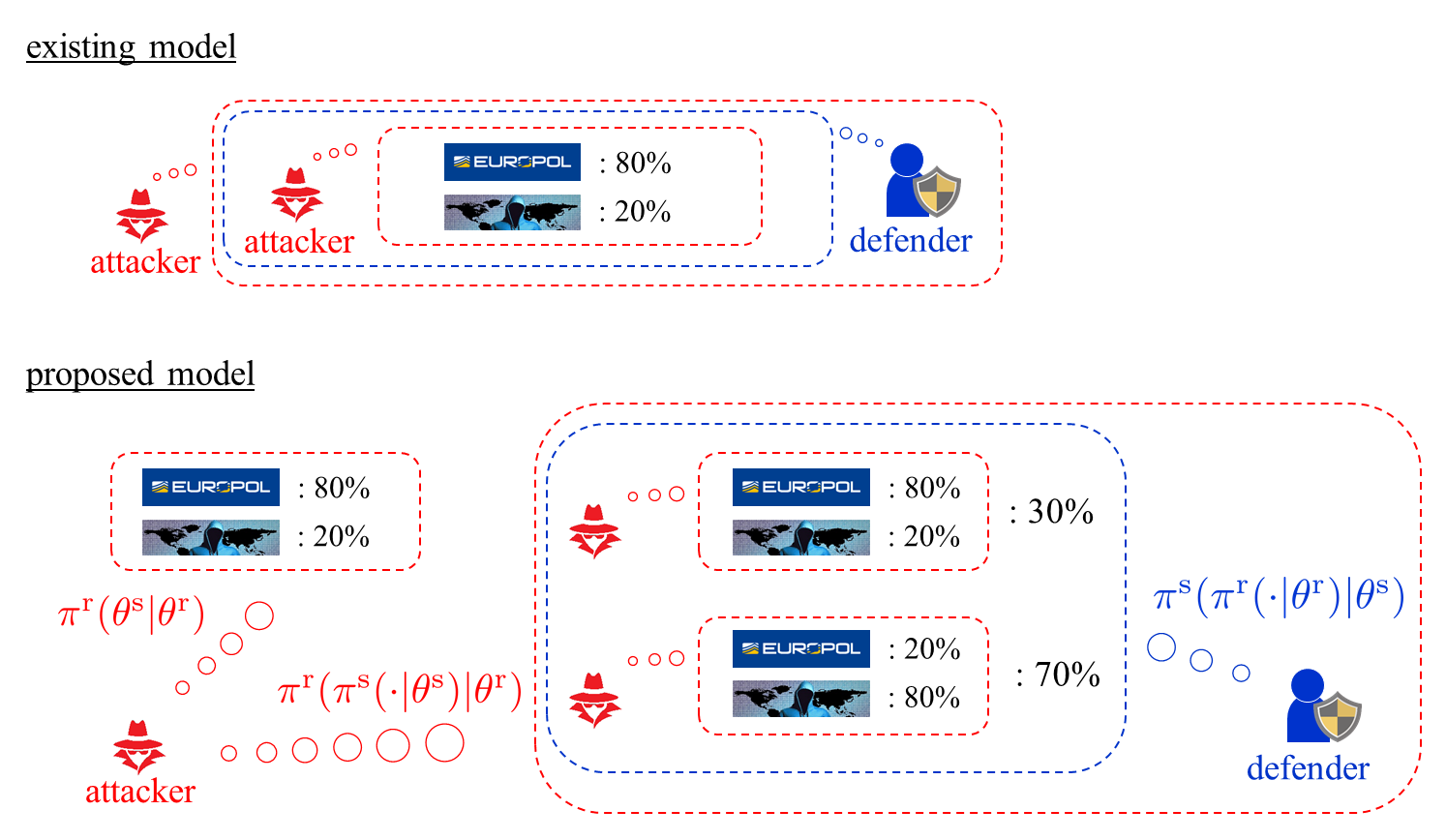
Modeling of Cyber Deception with Human's Cognitive Biases In 2021, FBI and Europol arrested 800 criminals by using encrypted communication devices that are developed by themselves as a "decoy". The key factor is that they succeeded to "deceive" criminals to believe that the device is beneficial despite of leakage risk. Such defender's proactive deception is referred to as defensive cyber deception, and several methods including honeypot have been developed. As a basic tool for data-driven cyber deception and quantitative analysis, mathematical models based on incomplete information games are employed. In incomplete information games, players do not know the game that is actually being played. In the example above, the uncertainty arises from the uncertainty about the provider of the device. Traditional models are built on the implicit premise that the human's recognition on the uncertainty, namely, what the criminal believes, is public information. However, this assumption is clearly unrealistic, and there exist biases between the criminal's recognition and the FBI's recognition in practice. From this perspective, this study has proposed a model of cyber deception that explicitly incorporates human's cognitive biases. In the model, an infinite chain of recognitions appears, such as how the criminal recognizes the uncertainty, how FBI recognizes the criminal's recognition, and how the criminal recognizes the FBI's recognition about the criminal's recognition. The notion to describe the mutual recognition is belief hierarchy, which plays a fundamental role in the proposed model. The proposed model induces equilibria that do not appear in the traditional models and leads to a precise evaluation of risks caused by cognitive biases in cyber deception. Related Publications
- H. Sasahara and H. Sandberg, "Epistemic Signaling Games for Cyber Deception with Asymmetric Recognition," IEEE Control Systems Letters, 2021.
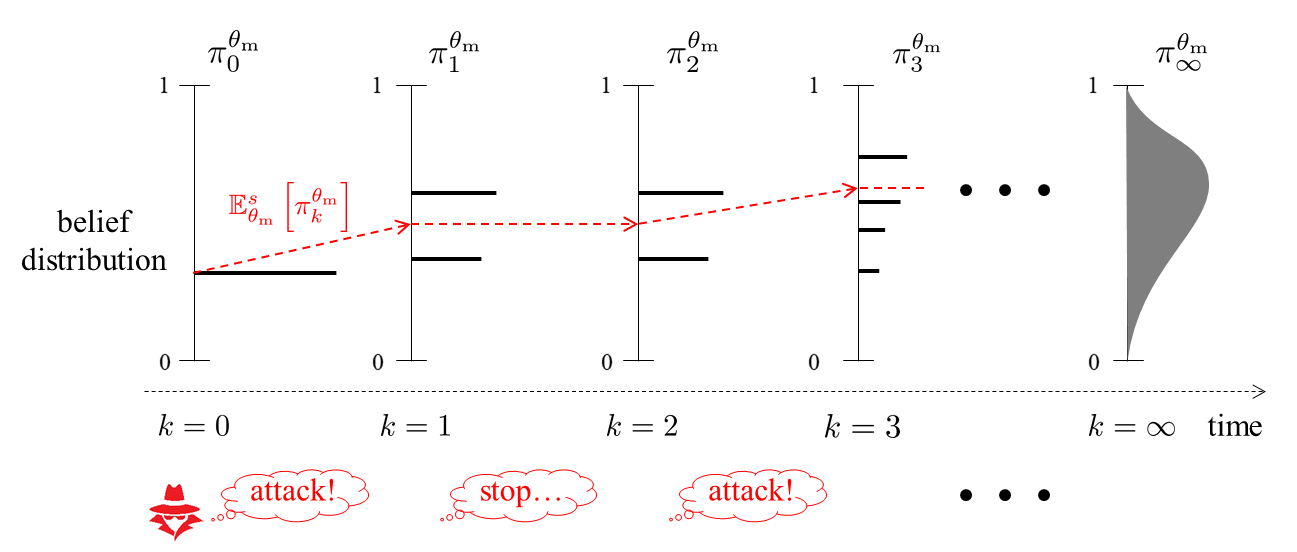
Asymptotic Analysis of Model-based Bayesian Incident Handlers Model-based security analysis helps the system designer to prioritize security investments. Probabilistic models of attacks and defenses, such as attack trees and attack countermeasure trees, have been proposed. The system dynamics can be incorporated into the model, which results in a general representation based on the class of Markov decision process. Using the model, several specific Bayesian defense mechanisms have been developed, including Bayesian intrusion detection. The fundamental idea is to choose appropriate counteractions by identifying the existence of an attacker and the plausible attack scenario based on Bayes' theorem. Those defense mechanisms naturally raise the question: "Can the defender with Bayesian inference be deceived?," or more specifically, "Do there exist any attacks that lead wrong inference?" Based on the framework of stochastic games with incomplete information, I have given the answer: "For any attacks, Bayesian inference asymptotically identifies the true scenario." The technical difficulty is that typical tools used in asymptotic theory such as law of large numbers and large deviation principle cannot be applied to our problem due to lack of independence or Markov property of the sample sequence. In this study, I resolved the problem and proved the claim by coming back to martingale theory. The result indicates the powerful defense capability achieved by model knowledge and validity of model-based defense mechanisms. Related Publications
- H. Sasahara and H. Sandberg, "Asymptotic Security using Bayesian Defense Mechanism with Application to Cyber Deception," IEEE Transactions on Automatic Control, 2024.
- H. Sasahara and H. Sandberg, "Asymptotic Security by Model-based Incident Handlers for Markov Decision Processes," Proc. IEEE Conference on Decision and Control, 2021.
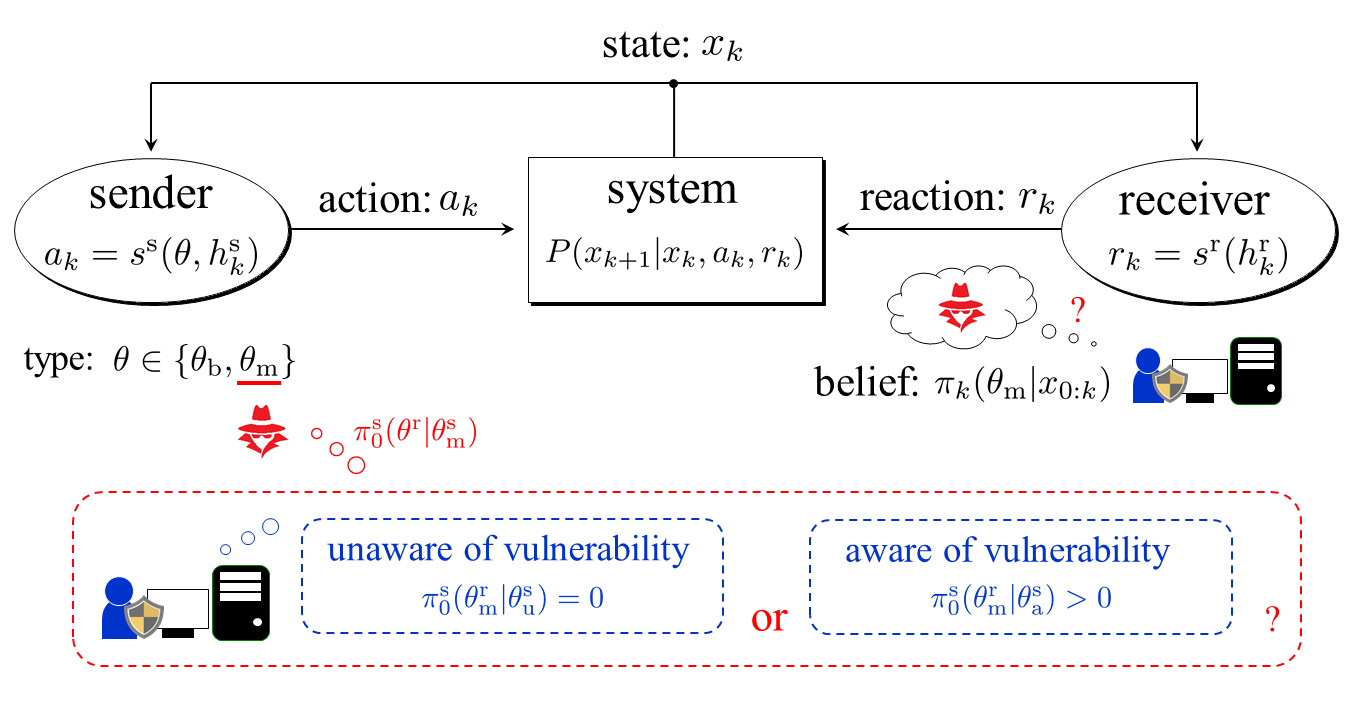
"Bluffing" against Zero-day Attacks utilizing Asymmetry in Knowledge and Recognition Zero-day attack is an attack that utilizes vulnerabilities unknown to the defender. It is believed that zero-day attack cannot be coped with once its exploit is carried out. However, this study has shown that its damage can be mitigated by using asymmetry in humans' knowledge and recognition. As a specific scenario, consider the case where the vulnerabilities are unknown to the defender but the fact that it is unknown to the defender is unknown to the attacker. In other words, the attacker has the recognition that the defender may be aware of the vulnerabilities and carrying out some counteractions. It is also assumed that the attack requires time and the attacker has to keep her existence during the attack. For example, lateral movement is an attack for a few months or years, and hence the scenario can happen in the real world. Then a natural attacker's strategy is to identify the defender's recognition through estimation of the defender's actions by observing the system behavior. On this premise, based on the framework of dynamic games with incomplete information, this study has mathematically proven that the attacker possibly stops the attack in the middle if the defender takes a strategy by which her recognition is concealed. The result is a rigorous description of "bluffing", which is done by humans in our daily life, and can possibly be extended to several intuitive defense methods. Related Publications
- H. Sasahara and H. Sandberg, "Asymptotic Security using Bayesian Defense Mechanism with Application to Cyber Deception," IEEE Transactions on Automatic Control, 2024.
- H. Sasahara, S. Sarıtaş, and H. Sandberg, "Asymptotic Security of Control Systems by Covert Reaction: Repeated Signaling Game with Undisclosed Belief," Proc. IEEE Conference on Decision and Control, 2020.
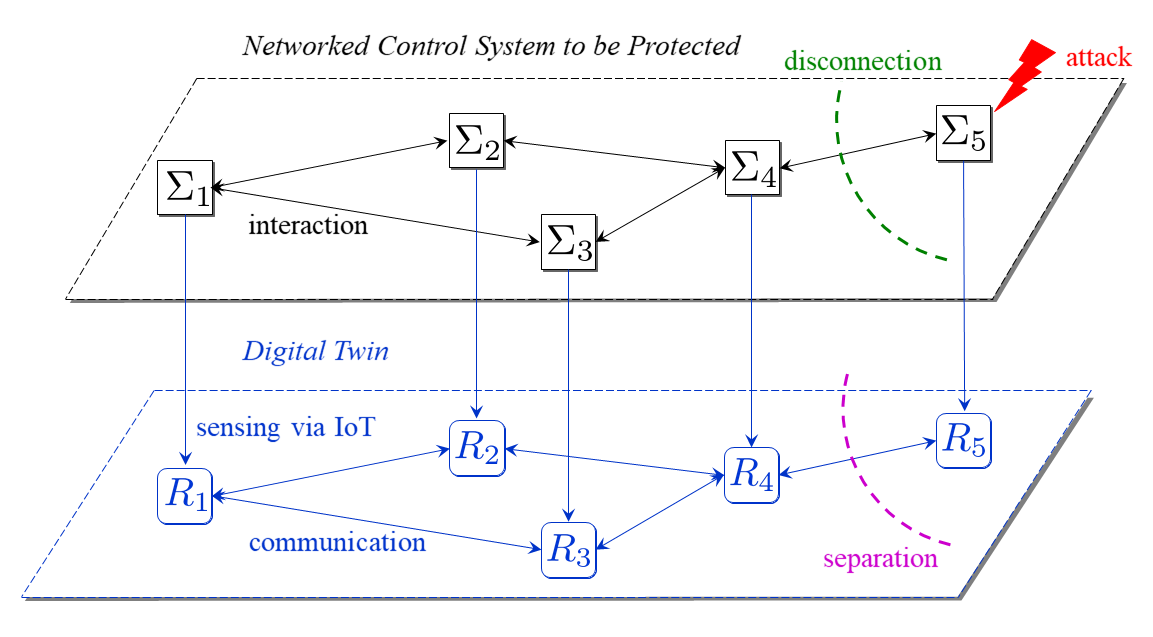
Integrated Design of Attack Detection and Containment for Networked CPS using Digital Twin Digital twin is a representation of physical system's behavior in the cyber space based on sensing through IoT (Internet-of-Things). Digital twin has been getting a lot of attention, and it has been shown that the concept is useful in the security. A basic application is attack detection, the idea of which is that to create a dynamical model that imitates the evolution of physical state and to confirm that data collected from the actual system coincide with the predicted time series. In this study, I have pointed out a problem arising from network topology variation caused by containment of attacks targeting a subsystem in a networked control system. There are feedback loops in the attack detector, and it is well-known in control engineering that responses of a dynamical system can possibly oscillate, i.e., the system can be made unstable, owing to feedback. In existing studies it is assumed that the system dynamics is fixed and the variation caused by containment has been completely disregarded. To solve the problem, I have proposed a framework of integrated design of attack detection and containment taking the dynamics variation into account. The effectiveness is verified through simulation using a CIGRE network model, a benchmark distribution network. Related Publications
- H. Sasahara, T. Ishizaki, J. Imura, and H. Sandberg, "Disconnection-aware Attack Detection and Isolation with Separation-based Detector Reconfiguration," IEEE Transactions on Control Systems Technology,. 2022.
- H. Sasahara, T. Ishizaki, J. Imura, and H. Sandberg, "Disconnection-aware Attack Detection in Networked Control Systems," Proc. IFAC World Congress, 2020.
Others: Resilience Analysis of Power Grids, Modular Design of Large-scale Control Systems, Compressed Sensing for Discrete-valued Signals, etc. I am doing researches on control theory, optimization, and signal processing in addition to CPHS security. Related Publications
- H. Sasahara, T. Ishizaki, J. Imura, H. Sandberg, and K. H. Johansson, "Distributed Design of Glocal Controllers via Hierarchical Model Decomposition," IEEE Transactions on Automatic Control,. 2023.
- M. Lindström, H. Sasahara, X. He, H. Sandberg, and K. H. Johansson, "Power Injection Attacks in Smart Distribution Grids with Photovoltaics," Proc. European Control Conference, 2021.
- H. Sasahara, T. Ishizaki, and J. Imura, "Parameterization of All Output-Rectifying Retrofit Controllers," IEEE Transactions on Automatic Control, 2021.
- T. Ishizaki, H. Sasahara, M. Inoue, T. Kawaguchi, and J. Imura, "Modularity-in-Design of Dynamical Network Systems: Retrofit Control Approach," IEEE Transactions on Automatic Control, 2021.
- H. Sasahara, T. Ishizaki, T. Sadamoto, T. Masuta, Y. Ueda, H. Sugihara, N. Yamaguchi, and J. Imura, "Damping Performance Improvement for PV-Integrated Power Grids via Retrofit Control," Control Engineering Practice, 2019.
- H. Sasahara, K. Hayashi, and M. Nagahara, "Multiuser Detection based on MAP Estimation with Sum-of-Absolute-Values Relaxation," IEEE Transactions on Signal Processing, 2017.